It’s been a while since cybercrime made it into the mainstream way of life. By now, we’ve heard many times that cybercrime evolves and adapts to always try and catch us off guard and fall for whatever the latest scam may be. Well, while that is indeed true, cybercriminals are realizing that sometimes, the old school tactics also still work. There have recently been a couple of new, old ways they have been successful at scamming us all.
With much of the attention with regard to phishing scams focusing on email and text, criminals have learned that maybe it’s time to go back to the ages old phone phishing scam. Why is that? Well, it’s because we are all pretty well educated on how to spot an email or text/SMS scam. It’s been drilled into our skulls not to click links and open attachments in email or texts. So, the criminals have started to use phone calls to steal our money, again. Using voice calls to scam victims is called “vishing” (short for voice phishing). The most well-known of these is probably the tech support scam. You know that one. Someone calls and informs you that your computer has some technical “issues” and they can come to your rescue and fix them. All it takes is for you to provide your credit card details and you will be saved.
In our digital world, the amount of personally identifying information (PII) posted online gives phone scammers an amazing amount of ammunition to pull off these attacks. Using details found on social media sites and business networking sites as bait, a convincing criminal can fairly easily establish some type of personal connection with the individual on the other end of a phone call. Take a look at your own profiles and try to determine what information could be used against you in a vishing attack. When the scammer gets a collection of PII from the victim, they can cobble it all together and make a scam attempt more likely successful.
To make a scam seem more believable, criminals can also change their caller ID so that those calls that come in appear to be from someone you know. You have probably seen a call come in to your phone that has the same area code and prefix as your number. Those rely on you believing that the call is coming from someone nearby, such as your neighbor. Sometimes, the numbers appear to be from a switch board and end with “00” intending to make you believe they are from your doctor, mechanic, etc. And recently, there have been scams using the voice to text translation features against victims. Voice to text converts a voicemail message that you have received into an email or text message that will be sent to you.
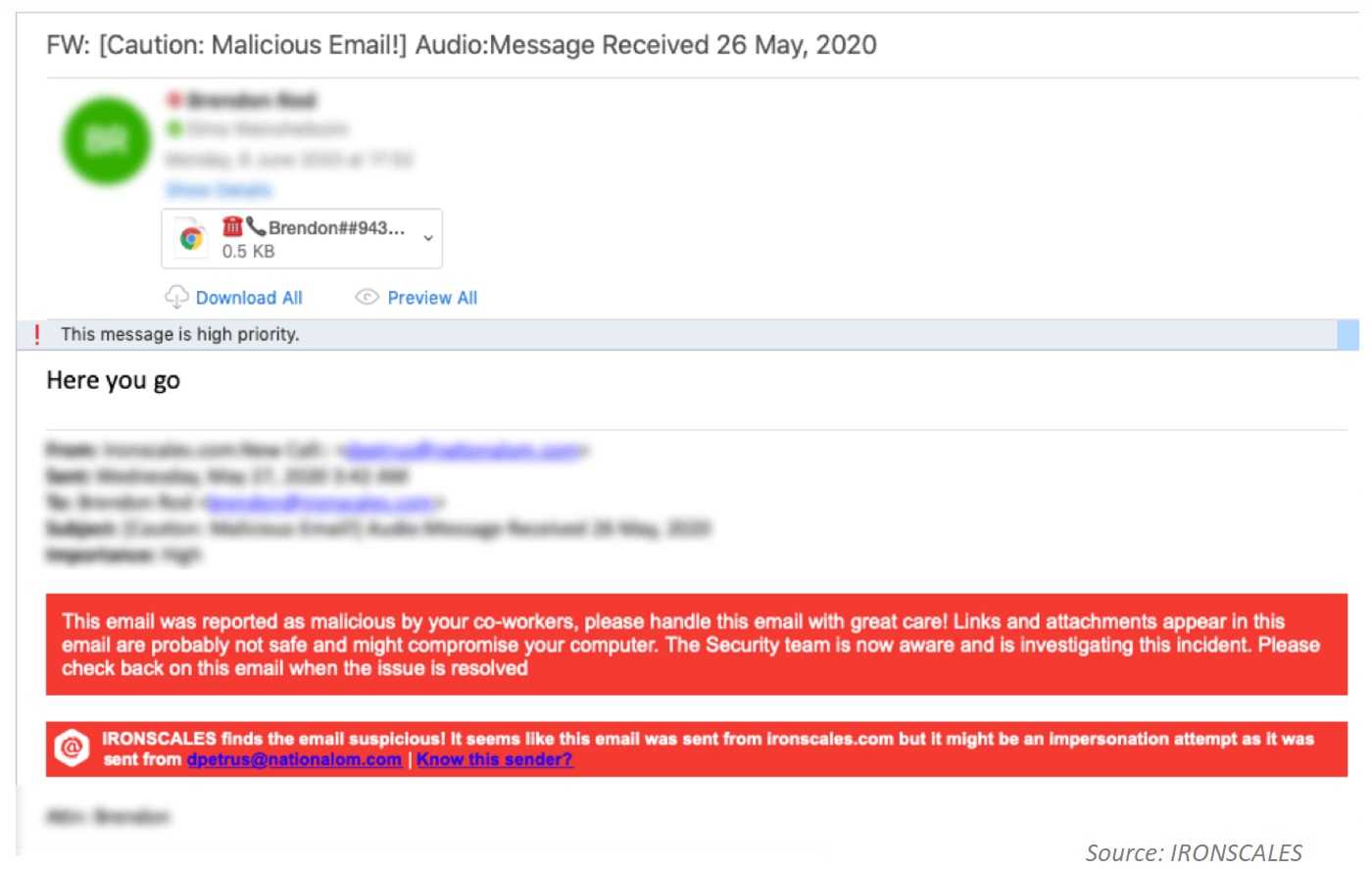
The company IRONSCALES found a widely distributed scam that takes advantage of this feature and resulted in over 100,000 fraudulent emails getting into peoples’ inboxes. Specifically, it translates a message that appears to be from a PBX (Private Branch Exchange) system, which is basically voicemail and are commonly used in offices. When we see a number that looks like it’s from one of these systems, we tend to trust it a little more. In addition, spoofing phone numbers is easy as pie these days, so they can make a number look like it came from anyone, anywhere. If you happen to look up the number, you may even find it to be the actual number of the organization the criminals are pretending to be from. They use personalized subject lines, appear to be from work and also use the recipient’s name, company name, and other coworker names, for example. Adding such personalization into the text also adds credibility to the illusion that they are legitimate. This scam is particularly effective at a time when more employees than ever are working from home and redirecting business related calls that go to their office voicemail to their email so they don’t miss them. That’s how this vishing scam has gained speed.
Another method being used in particular to pull off business email compromise (BEC) scams, is putting phone numbers into phishing email messages. Because it has been hammered into us not to click links and attachments, and we’re actually following that advice more often, scammers are sending plain text email messages claiming there is a problem with an invoice, a payment that was received, or some other notification that something may need to be addressed sooner than later. Then they add in a phone number to call for “help.” Well, instead of the number going to, say, FedEx, or one of your vendors, it goes back to the scammer, who convinces you that they are from the legitimate organization. You may give them company credit card details, banking information, or wire funds into their fraudulent account.
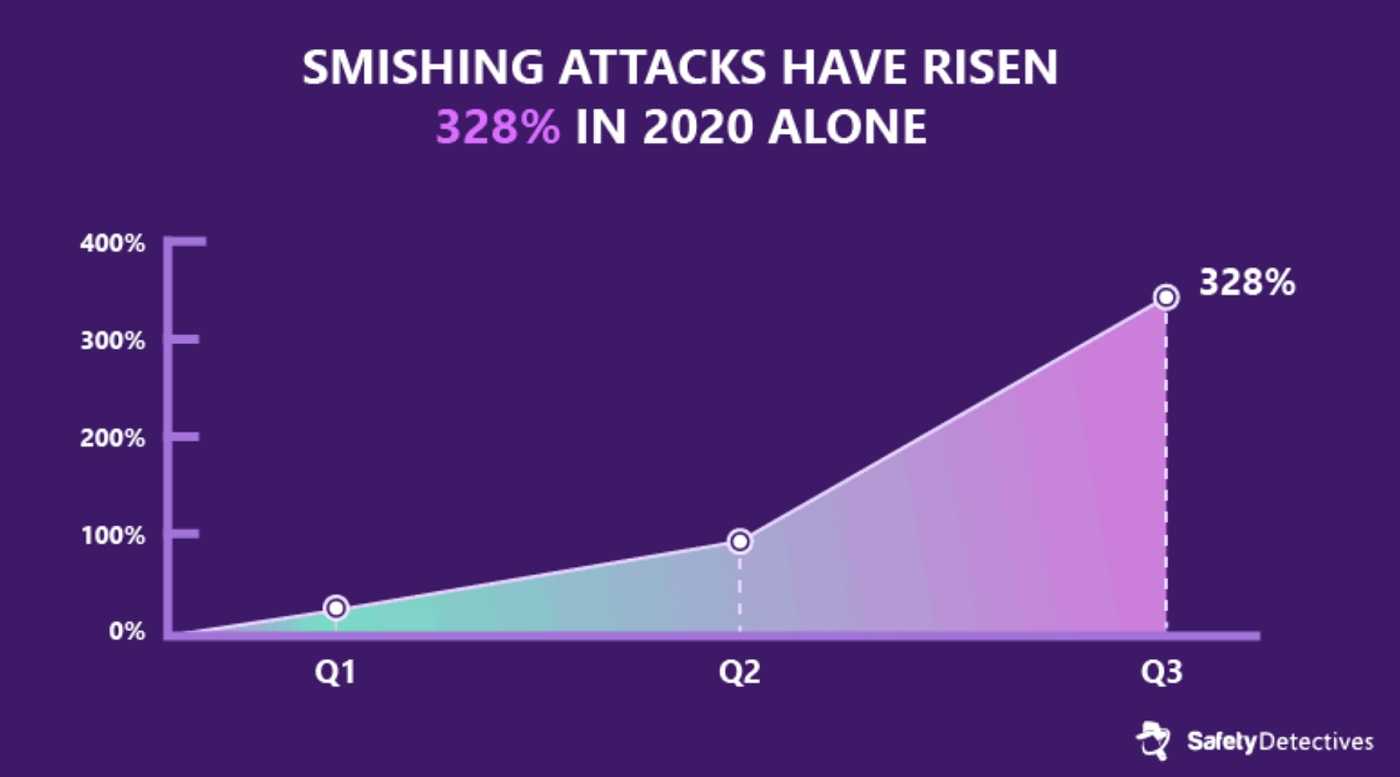
All of these types of scams take advantage of trust. We trust we know the caller or the phone number, so we are more likely to believe the criminals; who are getting better and better at phishing, vishing, and smishing (SMS phishing).
A very successful smishing scam hitting seemingly everyone lately is taking advantage of a popular Pier-to-Pier (P2P) payment service, Zelle. There are several flavors of this scam, but they result in a very similar process. If a target responds to the text scam in any way, the criminal will call the person to extract account credentials. Below is an example of a scam and the process executed.
Fortunately, there are ways to mitigate your risk of falling victim to all of these types of attacks:
Limit what information you provide on social media or any internet website. Try to use your general role, rather than title or specifics. This is especially important for those in accounting, finance, human resources, and C-level employees who have access to a lot confidential information about the organization and people within it. IT personnel are also often targeted.
- Even simply answering a phone call from an unknown number can let the criminals know the number is valid. They will keep trying once they know that to be true. The best defense is not to answer calls from unknown callers.
- If you get a translated voicemail message in your email, use contact information you already have saved or do your own search to find actual contact information for the sender. Don’t use phone numbers within the message or directly reply to one of these. Start a new email message, if that’s how you need to communicate back.
- To avoid getting caught up in BEC scams, have multiple people look at and approve wire, ACH or any spending requests, no matter who asks for it.
- Always keep your eyes and ears on high alert for any type of phishing. If someone contacts you out of the blue, it should trigger your Spidey sense. Do some due diligence to make sure it’s legitimate before providing any information to anyone.
Keeping you up to date on the latest scams. Just another way we are . . . Present for You.